AI TECHNOLOGIES FOR OFFENSIVE CYBER SECURITY
Scale capabilities of your penetration testing and
red team operations

Orchestration and automation pentest plateform
Orchestrate and automatically execute pentest techniques through complete attack paths, from initial access to the information system to post-exploitation of vulnerabilities, under the supervision of your experts.
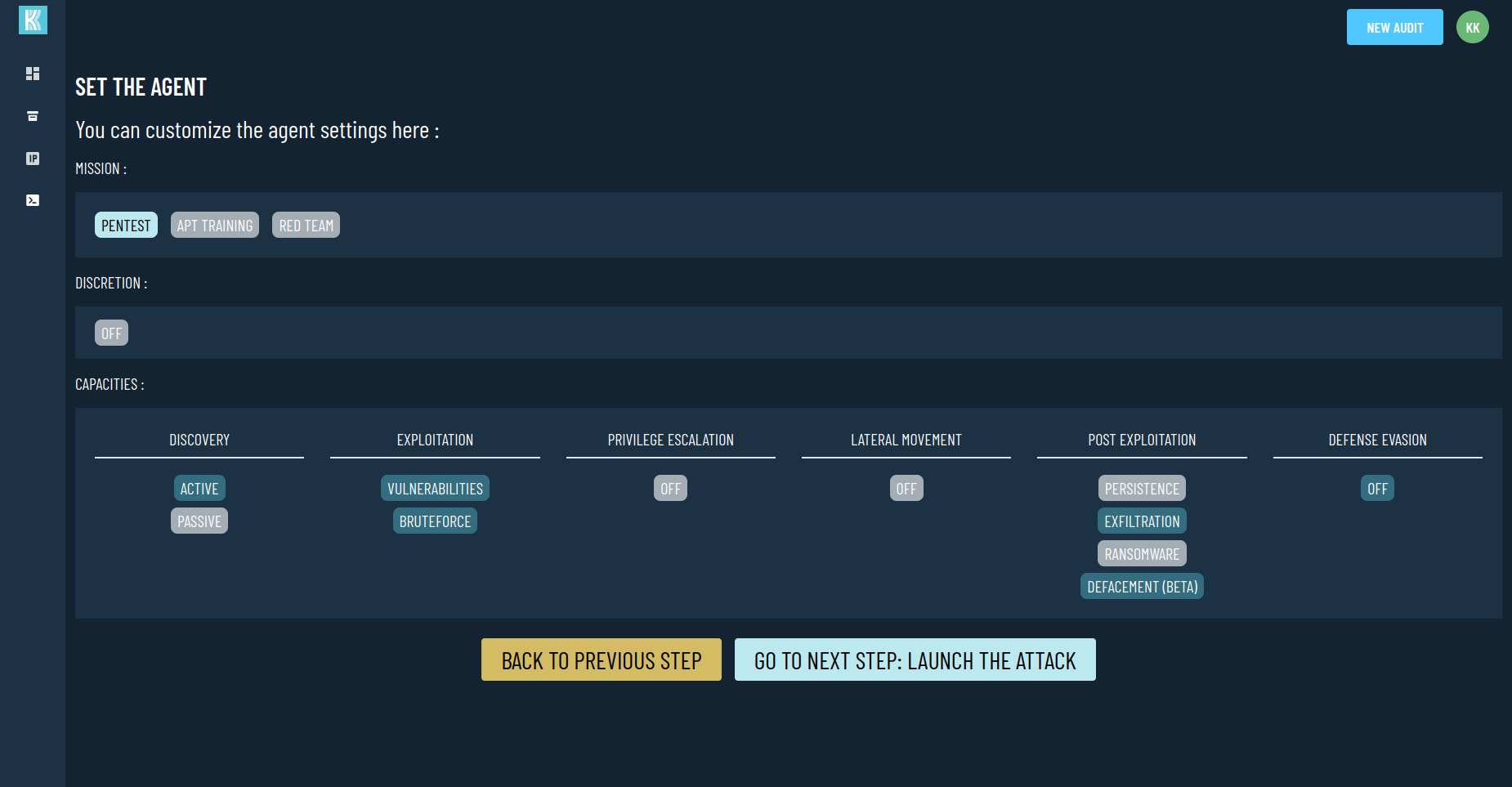
Configuration
Set the scope, customize techniques and tools used, define the objectives and the deployment modes
Suivi et pilotage
Suivez le test en temps réel, et validez les actions sensibles.
Sélectionnez et configurez les techniques et outils utilisées
Visualisez les logs détaillés pendant et après le test
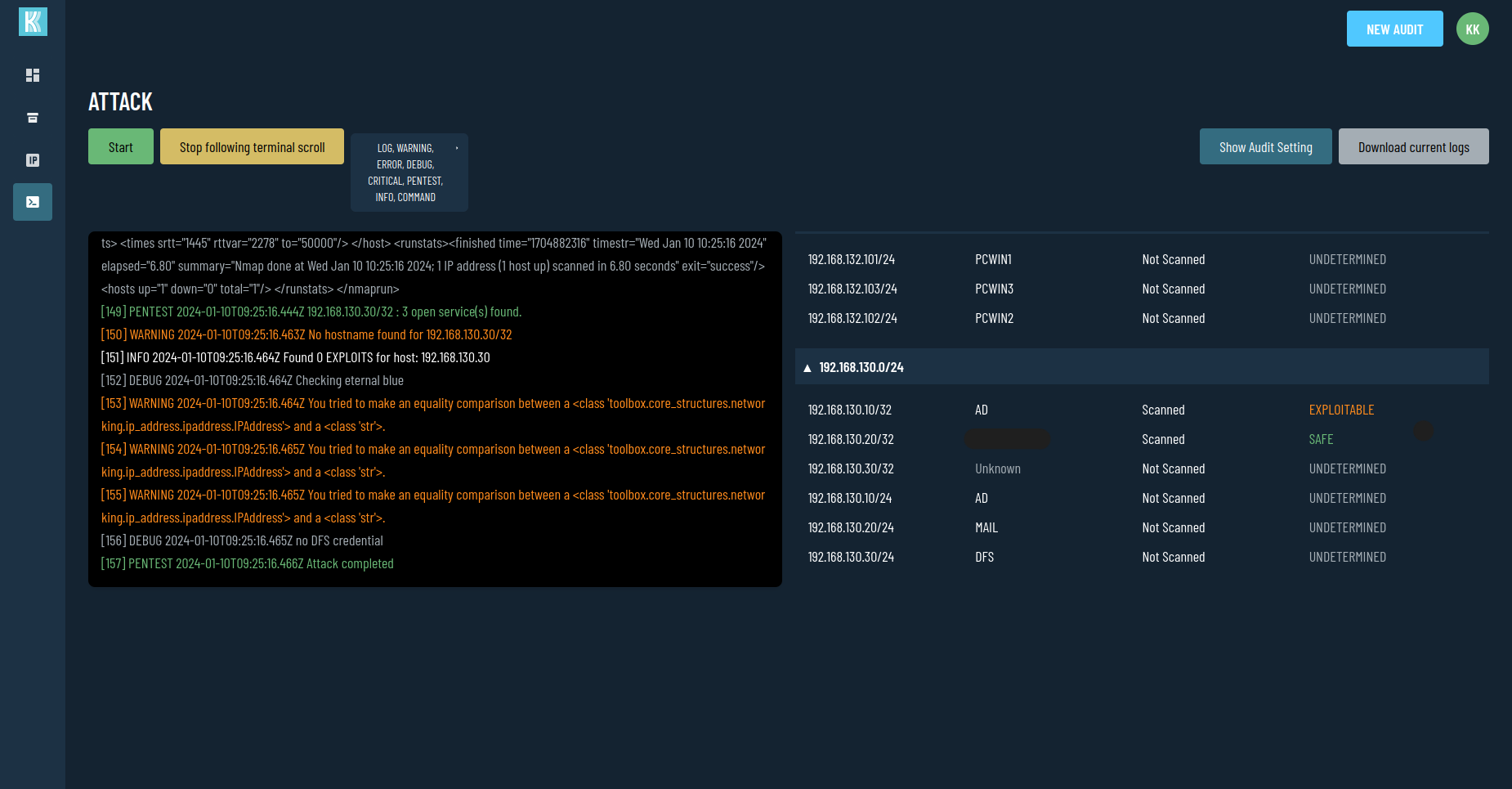
Control and monitoring
Monitor the test in real-time and validate sensitive actions.
View high value targets for manual tests.
Access detailed logs during and after the test.
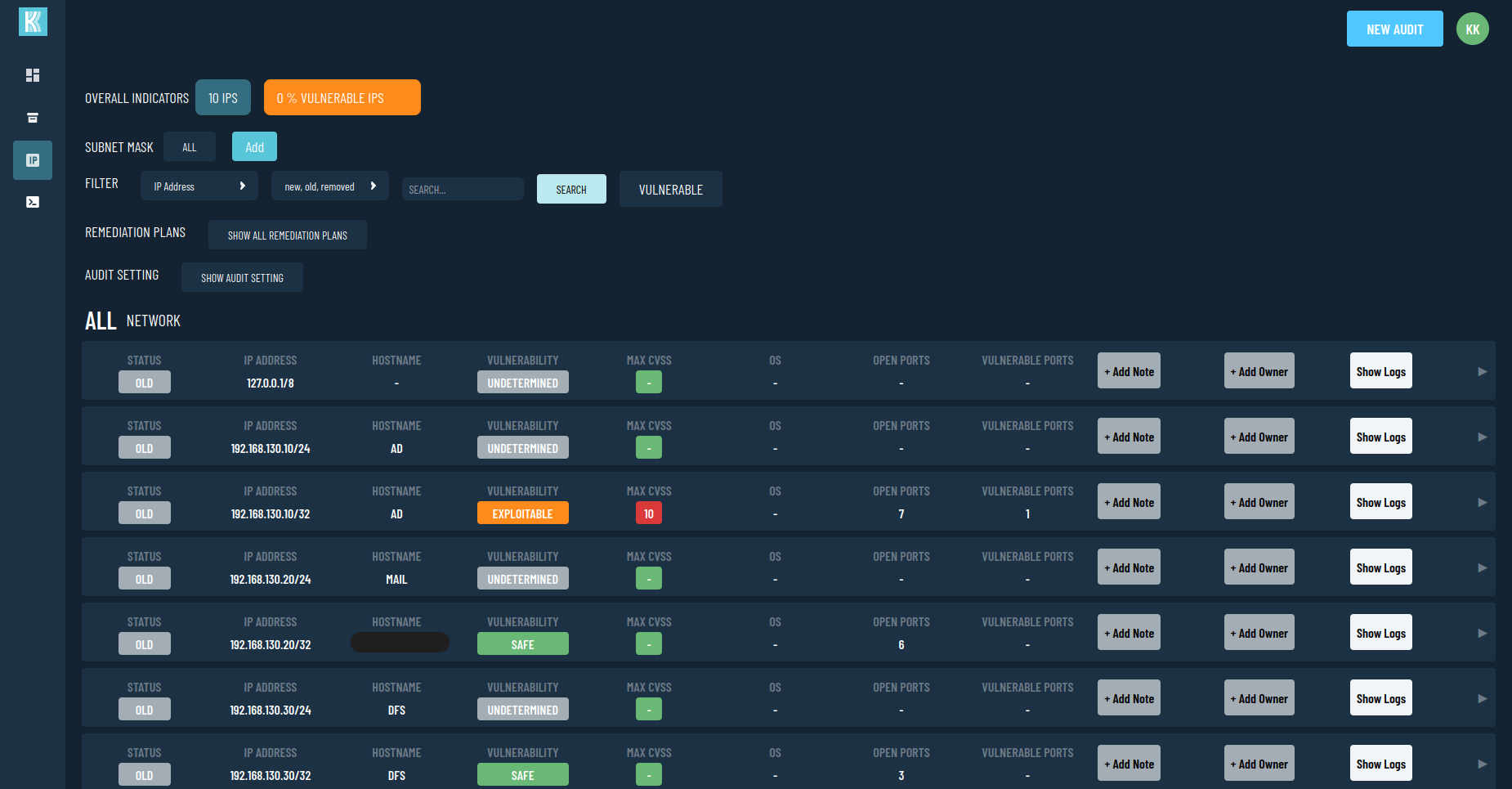
Reporting
Visualize attack paths and discovered networks & vulnerabilities.
Customize and share pentest reports.
BENEFITS

Productivity
Automatically launch all techniques integrated into our Hacker Toolbox, generate reports, and focus on the most complex tasks.

Scaling
Onboard junior pentesters through easy deployment tools, customized and validated by your experts

Availabilty
Delegate pentest skills to blue teams to replay pentests, and autonomous security validation.
TECHNOLOGIES
Automatic discovery of attack paths
Real-time responsiveness to changes in the IT environment
Complete transparency on the methods used
Customization of tools and their configurations
